Qakbot Reloaded
Qakbot is making the rounds once again, expanding its service as malware used by Initial Access Brokers (IAB). After a takedown attempt on Emotet and a recent pause of its operation, Qakbot and Bokbot/IceID have dominated the field as IABs. Qakbot, also known as QBot was a banking trojan at its inception but due to its modular design can be quite versatile. An important call out here is that recent cyber threat intelligence reveals Qakbot threat actors have modified their tactics, techniques, and procedures. This is precisely why we have created this new emulation.
Threat actors don’t work harder than they have to to accomplish their mission. If something is effective, they are not incentivized to change their tactics. Our new Qakbot emulation, similar to the one published earlier this summer, also uses an ISO file for Mark of the Web (MOTW) bypass. The July 2022 Qakbot sample uses an .LNK file that calls a legitimate Windows executable (calc.exe) to sideload the Qakbot loader. The Qakbot loader then calls regsvr32.exe to load the Qakbot payload DLL. We know for certain that the ISO -> LNK -> signed executable -> DLL sideload infection chain is still effective against many control stacks. The fact there is recent evidence that the threat actor researched and deployed new infection chains indicates that this new infection chain bypasses at least some control stacks (though we aren’t sure which ones).
The new infection chain spotted in the wild uses an ISO to continue bypassing MOTW. This is effective because MOTW uses alternate data streams (ADS), which are not available in CD filesystems, hence any files in the mounted ISO cannot possibly support this security feature. The only file visible to the user in the ISO is AS.js.
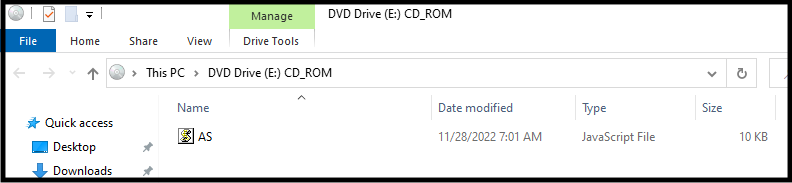
What the user sees when they mount the ISO
Presuming that the curious user clicks on AS.js, a PowerShell script is launched from a hidden directory in the ISO named ‘peseta’. The PowerShell script decodes a text file containing the contents of the Qakbot DLL, copies it into C:\users\public\test1.txt (don’t be confused by the .txt extension, this is a DLL), and then executed by calling rundll32.exe. It should be noted that the DLL is x86, so C:\windows\syswow64\rundll32.exe will be called to load it.
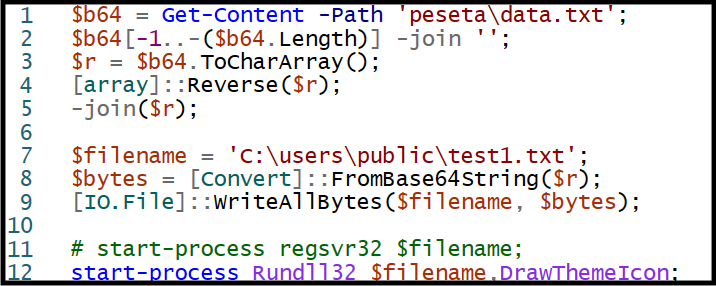
PowerShell Script to decode the DLL from “data.txt”
Again, even if you’ve run previous Qakbot emulations published by SCYTHE, we encourage users to run this one as well to validate their detection engineering. If this is your first Qakbot emulation (possibly because you’re a new SCYTHE customer), you should also run the July 2022 Qakbot emulation since that infection chain is still active in the wild.
Detection Opportunities
When threat actors change the way they deploy their malware, it likely requires updating our detection engineering. If all your existing detections alert on this emulation, good for you - you now know that you’re protected. If your detections don’t trigger alerting, don’t fret - running this emulation is the first step you can take in fine-tuning your alerting.
To be clear we are not providing detections or related SIGMA rules for steps 3 through 8 as we used PowerShell and the Mount-DiskImage commandlet to simulate the user double clicking on the ISO file. Any rules that trigger on this activity would instead be an artifact of our emulation and not something to base detection engineering on. As noted in Step 9, the .exe file is not something to signature but instead focus on the behavior seen after it is executed.
This post discusses active research by SCYTHE and other cited third parties into an ongoing threat. The information in this post should be considered preliminary and may be updated as research continues. This information is provided “as-is” without any warranty or condition of any kind, either express or implied.
References:
.jpg?width=352&name=635176f005ac4f8512364df3_Threat%20Thursday%20%20(3).jpg)