.jpg?width=352&name=5f91ad839ce583917c41afce_scy_tt_deeppanda_2%20(3).jpg)
Threat Emulation: Industroyer2 Operation
Jake Williams

Intro
Welcome to the May 2022 SCYTHE #ThreatThursday! This month we are featuring the recent Industroyer2 operation observed in Ukraine with a new campaign. Per the reporting from ESET, the Sandworm threat actor group was most likely responsible for deploying the Industroyer2 malware. For more information on the Sandworm group (in an easily digestible format), see Andy Greenberg’s book Sandworm linked here.
Executive Summary
There have been several attempts to disrupt Ukraine’s power grid since conflict began in its Eastern region early 20141. Russian-attributed threat actors deployed wiper malware against Ukrainian utilities in December 2015, targeting multiple power distribution substations. In December 2016, another cyberattack attributed to Russia used the original Industroyer malware (aka Crashoverride) to target utility transmission networks. ESET researchers who analyzed the original Industroyer malware assessed that the malware discovered by UA-CERT in 2022 has many of the same toolmarks. Although ESET has not shared the malware publicly, based on ESET’s historically reliable reporting we assert with high confidence that the Industroyer2 malware shares a common lineage with Industroyer.
This adversarial emulation campaign does not attempt to communicate with any Operational Technology (OT) or Industrial Control Systems (ICS) equipment. The campaign creates various artifacts on systems that were seen used by the Sandworm threat actor during deployment of Industroyer2 (as reported by UA-CERT).
Cyber Threat Intelligence
Profile:
Industroyer2 is a malware variant that is a more targeted version of Industroyer and its use has been linked to the threat actor known as Sandworm. Malpedia reports that Sandworm has been known to target ICS networks, including those associated with electricity and power generation2. This group has previously been linked to attacks on the Ukraine power grid in 2015 and 20163 and association with a Russian cyber military unit of the GRU.
Threat actor aliases:
Unit 74455, Black Energy,Voodoo Bear, Iron Viking
Targets:
Industroyer2 is slightly more narrowly scoped than the original Industroyer. The original malware had 4 distinct modules targeting specific ICS communication protocols (IEC 60870-5-101, IEC 60870-5-104, IEC 61850, and OLE for Process Control Data Access (OPC DA))4. Industroyer2, by contrast, is a standalone executable targeting IEC-104 controllers exclusively5. IEC-104 is used for power system monitoring and control over TCP and is mainly implemented in Europe and the Middle East.
Objectives:
We assess that a nation-state level threat actor (Sandworm) is leveraging Industroyer2 in an attempt to disrupt Ukraine’s critical infrastructure in support of Russia’s ongoing military operations. Per reporting by UA-CERT, the intrusion was discovered before destructive payloads were deployed against utility infrastructure.
Capabilities:
Industroyer 2 is highly configurable. Notable changes include the ability for the threat actor to embed customized configurations within the malware6. Unlike its predecessor, detailed configurations are hardcoded in its body rather than stored in a separate .INI file.
Industroyer2 also features process termination capability. Prior to connecting to targeted devices it will terminate a legitimate process, and append .MZ to the file name to prevent a re-start of said process7.
Once connected, Industroyer2 can craft various IEC-104 Application Service Data Unit (ADSU) messages to change the state of a remote device’s Information Object Addresses (IOAs) to ON or OFF. The level of detail in configuration, down to specific IOAs for a remote station, provide perspective into the comprehensive understanding of and potential visibility into a victim environment6.
Note: Because SCYTHE campaigns are crafted to be safe to execute in production environments, this campaign does not attempt to communicate with any ICS or OT devices. The capabilities discussed above are for reference only, as identified in the cited reports.
Summary of Actions Taken In Attack Emulation
The table below summarizes the actions taken by the Industroyer2 campaign. Per ESET reporting, the ARGUEPATCH binary loads obfuscated shellcode specified by a filename argument into memory. This version of the SCYTHE campaign does not simulate this behavior. Instead, the SCYTHE platform is used to create a random file consistent with the filenames in the UA CERT reporting and uses these filenames parameters to the benign executable used for testing.
| Action | Intended Result |
|---|---|
| Attempt connection to 91.245.255.243 | NDR or firewall may detect attempted connection to known C2 server observed in Industroyer2 campaign. |
| Attempt connection to 195.230.23.19 | NDR or firewall may detect attempted connection to known C2 server observed in Industroyer2 campaign. |
| Directory listing of C:\ | Primarily for SCYTHE user convenience to log whether non-standard directories c:\tmp and c:\dell existed before the campaign began. |
| Created file c:\perflogs\pa.pay | This file is used as a binary blob that is decrypted and loaded into memory in the Industroyer2 campaign. |
| Download an executable payload to C:\perflogs\vatt.exe | This executable is used to decrypt the pa.pay payload into process memory. The binary used for vatt.exe in this campaign is a benign executable. |
| Perform PowerShell Active Directory GPO enumeration | Some components of Industroyer2 were deployed via GPO. It is believed the PowerShell enumeration was used to locate GPOs to use for deployment and optionally to confirm that new GPOs created were visible to a sample target. |
| Create a scheduled task named “vatt” to execute vatt.exe | Per CERT-UA, scheduled tasks were used to launch the malware. The scheduled task created closely mimics that reported by CERT-UA. |
| Download an executable payload to c:\Users\peremoga.exe | This is the same executable used for vatt.exe. We do not know from reporting how many executable locations were used on a single target. The SCYTHE emulation plan uses variations of all the binary names observed. |
| Create file C:\users\pa1.pay | This file is used as a binary blob that is decrypted and loaded into memory in the Industroyer2 campaign. |
| Create a scheduled task named “Nezla” to execute peremoga.exe | Per CERT-UA, scheduled tasks were used to launch the malware. The scheduled task created closely mimics that reported by CERT-UA. |
| Download an executable payload to “C:\perflogs\40 115.exe” | This is the same executable used for vatt.exe. We do not know from reporting how many executable locations were used on a single target. The SCYTHE emulation plan uses variations of all the binary names observed. |
| Create a scheduled task named “40115” to execute “40 115.exe” | Per CERT-UA, scheduled tasks were used to launch the malware. The scheduled task created closely mimics that reported by CERT-UA. |
| Create file c:\perflogs\40 115.log | This file was observed by UA-CERT and is likely an output file from “40 115.exe.” UA-CERT did not specify the contents of the file. |
| Save the SYSTEM registry hive to C:\Users\Public\sys.reg | Save the contents of the SYSTEM hive, presumably for system recon and decryption of data in the SECURITY and SAM hives. |
| Save the SECURITY registry hive to C:\Users\Public\sec.reg | Save the contents of the SECURITY hive, presumably for cached domain logins |
| Save the SAM registry hive to C:\Users\Public\sam.reg | Save the contents of the SAM hive, presumably to enumerate account hashes and group membership information. |
| Create directory C:\dell | Create the non-standard directory C:\dell seen in UA-CERT reporting. |
| Create directory C:\tmp | Create the non-standard directory C:\tmp seen in UA-CERT reporting. |
| Download an executable payload to “C:\dell\108_100.exe” | This is the same executable used for vatt.exe. We do not know from reporting how many executable locations were used on a single target. The SCYTHE emulation plan uses variations of all the binary names observed. |
| Create file c:\dell\108 100.log | This file was observed by UA-CERT and is likely an output file from “108_100.exe.” UA-CERT did not specify the contents of the file. |
| Execute the command cmd /c C:\Dell\108_100.exe -o "C:\dell\108 100.log” | This command was observed by UA-CERT. SCYTHE executes a benign executable to generate telemetry with the same executable name and executable arguments. |
| Create file c:\dell\pa1.pay | This file is used as a binary blob that is decrypted and loaded into memory in the Industroyer2 campaign. |
| Download an executable payload to “C:\dell\watt.exe” | This is the same executable used for vatt.exe. We do not know from reporting how many executable locations were used on a single target. The SCYTHE emulation plan uses variations of all the binary names observed. |
| Execute the command cmd /c C:\Dell\watt.exe JRIBDFIMCQAKVBBP c:\dell\pa1.pay | This command was observed by UA-CERT. SCYTHE executes a benign executable to generate telemetry with the same executable name and executable arguments. |
| Download an executable payload to “C:\tmp\cdel.exe” | This is the same executable used for vatt.exe. We do not know from reporting how many executable locations were used on a single target. The SCYTHE emulation plan uses variations of all the binary names observed. |
| Execute the command cmd /c C:\tmp\cdel.exe | This command was observed by UA-CERT. SCYTHE executes a benign executable to generate telemetry with the same executable name and executable arguments. |
| User PowerShell to run the command rundll32.exe C:\windows\system32\comsvcs.dll,Minidump C:\users\public\mem.dmp full | Dump the process memory of lsass.exe using comsvcs.dll Minidump functionality. |
Detection Opportunities
Depending on your audit configuration, you may see event ID 4698 (new scheduled task creation) in the Security event log.
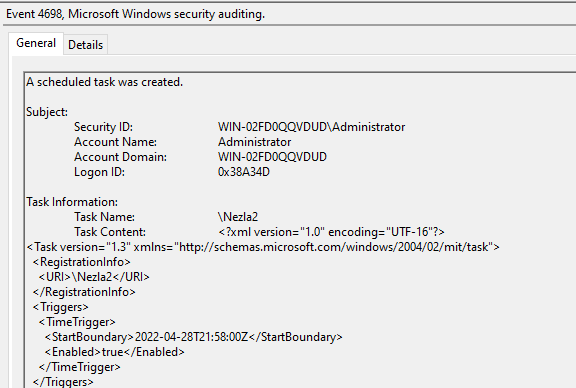
If the TaskScheduler/Operational log is enabled, additional logs showing the creation and execution of the scheduled tasks may also be present.
If Process Auditing is configured, event ID 4688 will track processes created (including those created by the scheduled tasks). If Sysmon is installed, process creation may also be logged in the Sysmon/Operational event log using event ID 1.
If file creation is monitored (e.g. object access) in the C:\windows\system32\tasks directory, the three scheduled tasks created (Nezla, 40115, and vatt) files should be detected. Additionally, the registry saved hives and lsass memory dump are all written into C:\users\public and might be logged with file creation monitoring.
PowerShell logging may capture the PowerShell creation of scheduled tasks and the attempts to reach the suspected C2 IPs. Detection engineers should not focus on any PowerShell detections since we do not have sufficient information from UA-CERT that PowerShell was the method used to create the scheduled tasks.
SIGMA Rules
The following SIGMA rules can be used for detection of actions taken in this campaign:
- Suspicious Schtasks From Env Var Folder
- Registry Dump of SAM Creds and Secrets
- Suspicious Service Binary Directory
- Execution from Suspicious Folder
- New TaskCache Entry
Additionally, this pattern can be used in command execution logs to discover executables running from an odd location (in this case C:\users\public):
- Matched_1: \\((Users|Documents and Settings))\\[^\\]{1,20}\.(exe|dll)
Clean-Up Steps
1. Remove the following files created as a result of our actions:
- C:\users\public\mem.dmp
- C:\users\public\sam.reg
- C:\users\public\sec.reg
- C:\users\public\sys.reg
- c:\windows\system32\tasks\40115
- c:\windows\system32\tasks\Nezla
- c:\windows\system32\tasks\vatt
2. Remove files we downloaded and do not intend to persist:
- C:\tmp\cdel.exe
- C:\Dell\108_100.exe
- C:\perflogs\40115.exe
- C:\dell\watt.exe
3. Files we created with the file module:
- C:\users\pa1.pay
- c:\perflogs\pa.pay
- c:\perflogs\40115.log
4. Nonstandard directories we (may have) created:
- C:\dell
- C:\tmp
Note: the campaign performs a directory listing of the C:\ before any directories are created. This allows the operator to confidently remove C:\dell and/or C:\temp knowing they were created exclusively by the SCYTHE campaign.
We have created a separate clean-up campaign with the above steps. You may run this separately or combine with the Industroyer2 campaign.
Respond
If any of the alerts are detected in the environment, the response team should determine the depth of the Kill Chain, collect artifacts, and answer the following questions:
- Was the installation successful?
- What are the persistent mechanisms?
- Is Command & Control (C2) successful?
- What are the domain names, IP addresses, ports, and protocols used?
- Are there observations of Actions on Objectives (AOO)?
- What are they?
- Did the actor laterally move?
- Was sensitive data taken?
- Usernames, Passwords, Other?
- What caused the initial compromise?
- How was it delivered?
- What was exploited?
- Vulnerability, Control, Human?
Once it has been determined how deep the intrusion goes, containment, eradication, and recovery should begin. After recovery, lessons learned should drive additional courses of action (COAs) to thwart the threat should it return, such as implementing additional security controls. As always, please follow your organization's response plan and evidence retention policies. We also recommend leveraging NIST SP 800-61 Rev. 2.
This Threat Thursday post discusses active research by SCYTHE and other cited third parties into an ongoing threat. The information in this post should be considered preliminary and may be updated as research continues. This information is provided “as-is” without any warranty or condition of any kind, either express or implied.
About the Author
The SCYTHE CTI team, including Jake Williams, Kristen Cotten, and Nathali Cano contributed to this report. Christopher Peacock assisted with QA and performed detection engineering.
About SCYTHE
SCYTHE provides an advanced attack emulation platform for the enterprise and cybersecurity consulting market. The SCYTHE platform enables Red, Blue, and Purple teams to build and emulate real-world adversarial campaigns in a matter of minutes. Customers are in turn enabled to validate the risk posture and exposure of their business and employees and the performance of enterprise security teams and existing security solutions. Based in Arlington, VA, the company is privately held and is funded by Gula Tech Adventures, Paladin Capital, Evolution Equity, and private industry investors.
References
- The Russian Invasion of the Crimean Peninsula, 2014–2015: A Post–Cold War Nuclear Crisis Case Study (jhuapl.edu)
- https://malpedia.caad.fkie.fraunhofer.de/actor/sandworm
- https://www.wired.com/story/russian-hackers-attack-ukraine/
- Industroyer: Biggest threat to industrial control systems since Stuxnet | WeLiveSecurity
- Industroyer2: Nozomi Networks Labs Analyzes the IEC 104 Payload
- INDUSTROYER.V2: Old Malware Learns New Tricks | Mandiant
- Industroyer2: Industroyer reloaded | WeLiveSecurity
Latest Posts
Related Threat Thursday
.jpg?width=352&name=5f91ad839ce583917c41afce_scy_tt_deeppanda_2%20(3).jpg)

Threat Thursday: 2024 in Review
The cybersecurity landscape continues to evolve, with threat actors targeting critical...

#ThreatThursday - menuPass with special guest Shane Patterson
For this #ThreatThursday is menuPass! Tim Schulz caught up with Shane Patterson to discuss MITRE...






